In case y'all haven't been following the PRISM scandal that broke last week, here's an article about it from no less than the Washington Post:
http://www.washingtonpost.com/investigations/us-intelligence-mining-data-from-nine-us-internet-companies-in-broad-secret-program/2013/06/06/3a0c0da8-cebf-11e2-8845-d970ccb04497_story.html
The story linked above just focuses on the internet part of the Feds' spying. The original story by the U.K.'s Guardian focused on the phone spying...
http://www.guardian.co.uk/world/2013/jun/06/nsa-phone-records-verizon-court-order
...and only briefly mentioned that the spying program also "implemented a bulk collection program of domestic...internet and email records." Subsequent investigation has revealed that the internet and email spying has been going on for at least the past six years.
Microsoft was first to join* this spy ring in 2007, followed by Yahoo, Google, Facebag, PalTalk, YouTube, Skype, AOL, and finally Apple (in 2012, October). Please note that the companies listed below are providing information that includes email. Here's one of the PowerPoint slides from the National Security Agency (NSA) that was leaked when the story broke:
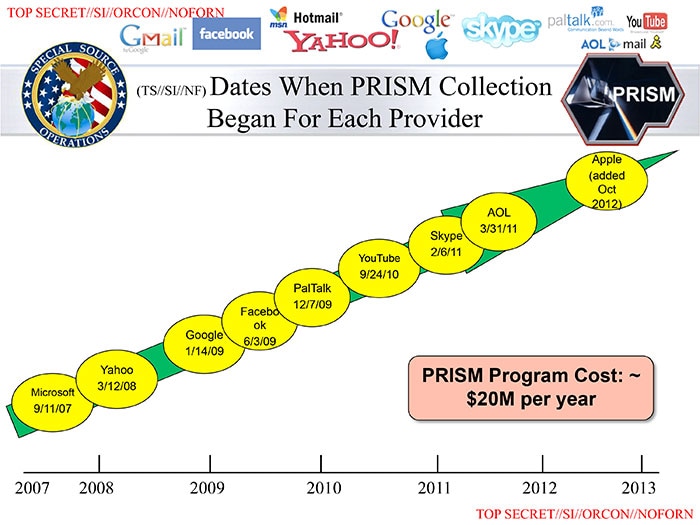
NOTE: The rest of the slides are here: http://www.washingtonpost.com/wp-srv/special/politics/prism-collection-documents/All of the companies listed above have denied participation in the PRISM program. Either they're lying (which is bad enough), or the Feds managed to infiltrate their data servers without their knowledge (which is far worse). Any way you cut it, this is menacing stuff.
Notice the "TOP SECRET" notation at the bottom right of the slide above. Get it? The Feds didn't want you to know they were spying on you. This is not a partisan political issue. Mr. Obama is just as guilty as his predecessor; Mr. Bush signed the law that made it "legal".
I leave the ramifications of this kind of massive surveillance of millions of private citizens to your imagination.

http://www.washingtonpost.com/investigations/us-intelligence-mining-data-from-nine-us-internet-companies-in-broad-secret-program/2013/06/06/3a0c0da8-cebf-11e2-8845-d970ccb04497_story.html
The story linked above just focuses on the internet part of the Feds' spying. The original story by the U.K.'s Guardian focused on the phone spying...
http://www.guardian.co.uk/world/2013/jun/06/nsa-phone-records-verizon-court-order
...and only briefly mentioned that the spying program also "implemented a bulk collection program of domestic...internet and email records." Subsequent investigation has revealed that the internet and email spying has been going on for at least the past six years.
Microsoft was first to join* this spy ring in 2007, followed by Yahoo, Google, Facebag, PalTalk, YouTube, Skype, AOL, and finally Apple (in 2012, October). Please note that the companies listed below are providing information that includes email. Here's one of the PowerPoint slides from the National Security Agency (NSA) that was leaked when the story broke:
- * To be fair, it's still not clear whether Microsoft or any of the other companies voluntarily participated in PRISM.

NOTE: The rest of the slides are here: http://www.washingtonpost.com/wp-srv/special/politics/prism-collection-documents/
Notice the "TOP SECRET" notation at the bottom right of the slide above. Get it? The Feds didn't want you to know they were spying on you. This is not a partisan political issue. Mr. Obama is just as guilty as his predecessor; Mr. Bush signed the law that made it "legal".
I leave the ramifications of this kind of massive surveillance of millions of private citizens to your imagination.

